Blockchain makes big promises – and raises big questions
 Although blockchain technology has generated a lot of buzz, it is not widely understood. To begin with, the blockchain concept is not entirely new. Instead, it is an updated version of the mutually distributed ledger (MDL) applications that have existed for decades. However, MDL was always too unwieldy and unsafe for large-scale use.
Although blockchain technology has generated a lot of buzz, it is not widely understood. To begin with, the blockchain concept is not entirely new. Instead, it is an updated version of the mutually distributed ledger (MDL) applications that have existed for decades. However, MDL was always too unwieldy and unsafe for large-scale use.
When the anonymous entity known as Satoshi Nakamoto created the cryptocurrency bitcoin in 2008, they also built blockchain, the system that supports bitcoin.
In a blockchain network, updatable data is distributed across a number of computers. Users are connected only to the other users. Each item in the network is reconciled continually and current information is always available to users.
Blockchain-type applications are available in several versions and from different vendors. The name represents a host of variations that developers have produced since the bitcoin people introduced blockchain. As other digital monies have appeared, systems resembling blockchain have been developed to support them. Now blockchain versions have spread to industries and vertical uses far beyond the realm of cryptocurrencies. There are significant differences between these systems, but by and large they fit the same general mold.
A blockchain is a peer-to-peer (P2P) ledger system that distributes data via a private network of computers. A series of network nodes transmit packets of information called blocks. These are linked and verified by cryptographic validation. Each block references the previous block by a hashing function, forming a continuous chain. Blockchain technology is designed to offer significant improvements over MDL in safety, stability, and ease of use.
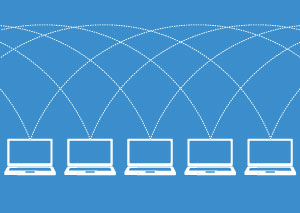 Content is shared directly between users, with no intermediary. Everyone in the network can see the same data and the same history as everyone else. Old items are preserved permanently and new ones are added irreversibly.
Content is shared directly between users, with no intermediary. Everyone in the network can see the same data and the same history as everyone else. Old items are preserved permanently and new ones are added irreversibly.
Content is not stored in any one place, nor is it managed by any single entity. It exists only on the computers within the network.
Information is available to all parties and multiple users can work on the same document simultaneously. There is no losing track of versions or being out of sync with other participants.
Information can be shared but not copied or captured by anyone outside the network. Blockchains are protected via encrypted public and private keys, which are randomly generated strings of numbers. A public key is a user’s address and a private key is the user’s password
Numerous uses for blockchain have arisen, often served by specialized vendors. Here are some examples.
- Contracts can be made to execute automatically when certain conditions are met, with all parties simultaneously informed in real time.
- Crowdfunding will use blockchains to create streamlined P2P transactions.
- Government transparency could improve election fairness and public funding activities.
- Supply-chain auditing can more easily validate or debunk claims made by vendors.
- File storage can be made more secure.
- Trend prediction can be made faster and more accurate by capturing and utilizing “wisdom of the crowd” data.
- Intellectual property can be better protected and more safely distributed.
- Distribution of copyrighted material can be improved by strengthening peer-to-peer transactions. In particular, this applies to the distribution of music.
- The Internet of Things (IoT) can be made simpler and more efficient as digital devices and components are better-connected.
- Money-laundering can be reduced by widespread and verifiable accessibility of financial information.
- Stock trading can be better managed and controlled.
- IT auditing can be simplified.
Problems and considerations
As with any emerging technology, blockchains present challenges, and more are likely to arise. Some of these we can anticipate, others will be surprises.
- With its private-access-only structure, blockchain offers enhanced data protection, but long experience tells us that anything can be hacked, in some form or fashion.
- Human error always presents risks. In blockchain applications, the intersection between the user and the network is the most dangerous endpoint. This highlights the need for diligent commitment to best practices. Also, for a blockchain network to succeed, trust between participants is imperative.
- Blockchains often connect different companies, so each needs to be confident that other network partners have the space, technical resources and dedicated staff to hold up their end of the bargain.
- Blockchain technology is still new. Slipshod development processes and the incidence of bugs and losses are predictably at their highest during the early stages of any technology’s evolution.
- Some blockchain developers release products before they are market-ready. Users complain about scalability, latency and security problems, as well as faulty logging, monitoring and random-number generation.
- The easiest and most obvious way for hackers to break into a blockchain is to steal public and private keys. By definition, these keys have to be stored outside the blockchain, on a scrap of paper, a computer or other device, all easy targets.
- Natural disasters and other types of physical damage are always possible, and are as threatening to blockchain technology as to any other component of an organization’s IT setup.
- Blockchain is effective in multi-party peer-to-peer settings but may not be an effective tool for individual companies in which data sharing with other entities is unimportant. These organizations may only need databases to share information internally.
 Backup and recovery
Backup and recovery
Blockchain’s private-network structure offers significant data protection, but the need for strong backup and recovery capabilities is always paramount. Any system can be compromised by hackers, physical disasters, server breakdowns, human errors, intentional sabotage and other causes. Despite its benefits, blockchain technology is not intended primarily as a bulwark against such potential threats. The only reliable safeguards are effective cloud backup and disaster recovery capabilities.
- Just as blockchain applications are expanding, cyber threats continue to multiply.
- The addition of blockchain technology to a system makes it more complex, so disaster recovery should accommodate that complexity.
- Ransomware hackers have their eye on target-rich blockchain networks, notably those armed with RaaS (ransomware as a service).
- Downtime can be especially dangerous for blockchain elements within a system, since one of their main advantages is high availability.
- Blockchain adds another potentially dangerous endpoint data backup element.
In addition to providing necessary tools, our consulting and strategy capabilities are key to planning your business continuity processes in the blockchain era.
To learn more about data protection, email us at info@renovodata.com or give us a call at 1 877 834 3684.